Single Sign-On
Single Sign-on (SSO) is a session and user authentication process. It allows you to access multiple applications by logging in only once with one set of login credentials.
The SSO feature supports applications using the same identity service.
For example: Application1 and Application2 use a Google Identity Provider. When you sign in to Application1 by using the credentials for the Google Identity Provider, you need not sign in to Application2. You will be automatically signed in to Application2.
- Single Sign-On is supported for Android, iOS, and Web platforms.
- When an Identity Service is mapped using the Data Panel in Quantum Visualizer, the SSO feature does not function.
Use Case
To understand the functionality of the SSO feature, consider two applications namely Calendar app and Task app using the same identity provider. The following flow diagram illustrates how SSO feature works on user's device at runtime:
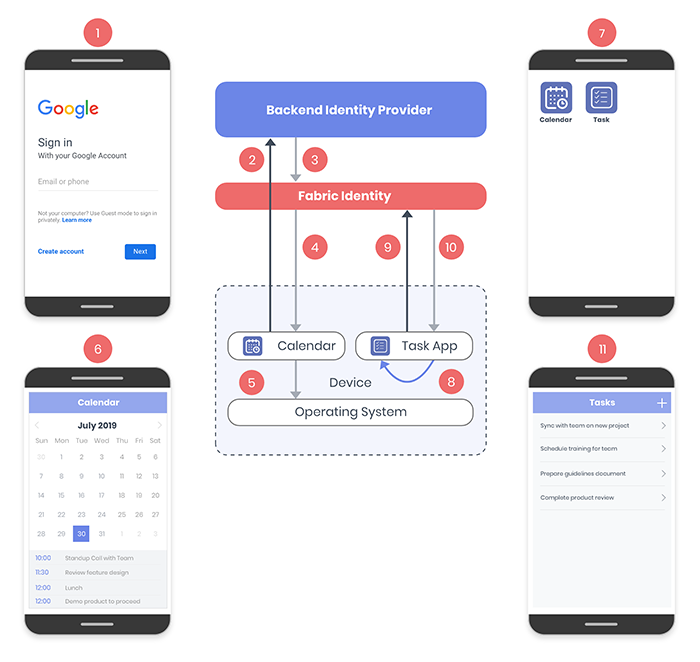
The workflow of these applications is as follows:
- The user first starts the Calendar app, and then types the user credentials to log on to the app.
- The Calendar app sends the credentials to the Backend Identity Provider for authentication.
- On receiving the credentials, the Backend Identity Provider returns an authentication token to Quantum Fabric Identity.
- Quantum Fabric Identity then sends an SSO token to the Calendar app.
- The Calendar app stores the SSO token on the device.
- On successful authentication, the Calendar app loads the user's calendar.
- The user then starts the Task app.
- The Task app fetches the SSO token from the device and sends it to Quantum Fabric Identity for validation.
- After the SSO token is validated, Quantum Fabric Identity authenticates the user and sends the SSO token to the Task app.
- Finally, the Task app is launched without the user having to log on.
SSO Configuration
To configure SSO in your applications, perform the following tasks:
- Enable SSO in Quantum Fabric Console
- Configure Client Applications on Quantum Visualizer
- Configure SSO Permissions for Native Platforms
Enabling SSO in Quantum Fabric Console
To enable SSO in Quantum Fabric Console, follow these steps:
- Sign in to Quantum Fabric Console.
- Go to the Apps tab and open the app for which the Single Sign-On feature is to be enabled.
- In the Identity section of the services, click the contextual menu of the required service.
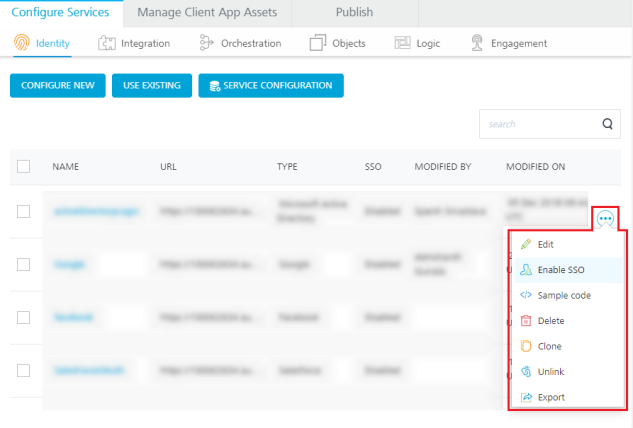
- A list of options appears. Select the Enable SSO option from the list.
- After the SSO feature is enabled, republish the app for the SSO feature to come into effect.
Configuring Client Applications on Quantum Visualizer
The client applications are built on Quantum Visualizer and they interact with the Quantum Fabric server using the Quantum Fabric SDK.
IMPORTANT: Ensure that the Quantum Fabric application, which you have configured earlier is associated with your Quantum Visualizer project.
To enable SSO on the client application for login call, add the following code in Quantum Visualizer:
//Sample code to authenticate to Quantum Fabric client
var serviceName = "identity_service_name";
var identitySvc = KNYMobileFabric.getIdentityService(serviceName);
var options = {};
var loginOptions = {};
options["userid"] = "userid";
options["password"] = "password";
loginOptions["isSSOEnabled"] = true;
option["loginOptions"] = loginOptions;
identitySvc.login(options, function(response) {
kony.print("Login Success: " + JSON.stringify(response));
}, function(error) {
kony.print("Login Failure: " + JSON.stringify(error));
});
Configuring SSO permissions for Native Platforms
The SSO tokens are stored in shared space/keychains of the devices. You must configure application settings to ensure that these tokens are shared among all the SSO enabled apps so that the SSO is implemented and other applications can access these tokens.
Permissions in Android Devices
Permissions in Android Devices
For the SSO feature to work in the Android devices, follow these steps.
- Go to Project Settings > Native > Android Mobile/Tablet.
- In the SSO section,
- Select the Enable SSO check box.
- In the Organization ID box, type your organization ID.
NOTE: The Organization ID must be unique for every organization so that the SSO token is shared amongst a particular organization only.
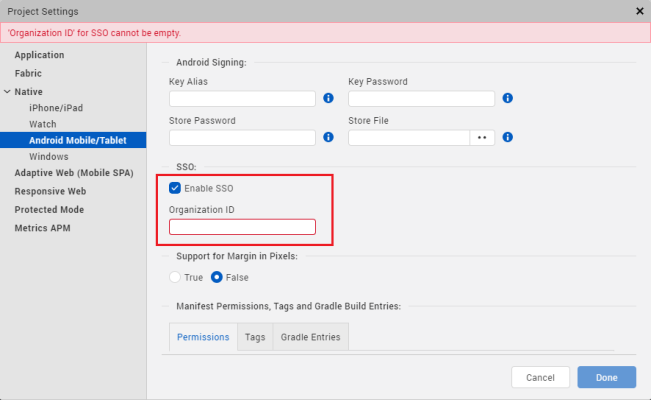
- Click Done to save the changes.
-
Repeat the steps for each app that needs SSO capability to be enabled.
Permissions in iOS Devices
To configure permissions for iOS devices, follow these steps:
- Open the project in Xcode.
- In the Capabilities section, enable the Keychain Sharing option and enter a name for the keychain group.

- Go to Info tab in Xcode project. Create a new property in the Custom iOS Target Properties section called
KONY_SHARED_KEYCHAIN_GROUPof the string data type. Set the name of the keychain group created in the previous step as value for the new property. For example,KONY_SHARED_KEYCHAIN_GROUP = PM7352S8QE.com.kony.sso

Here,
PM7352S8QEis an Organizational Unit value in the certificate, which can be obtained from the developer certificate.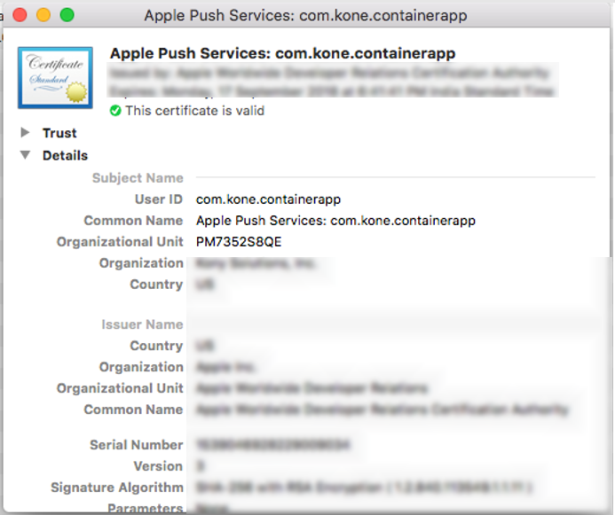
- Repeat the steps for each app that needs SSO capability to be enabled.
IMPORTANT: For all apps that intend to share the same SSO group, the key name string must be the same. The key name string must be different for different SSO groups.
Additional Information
- For Android, if you upgrade your Visualizer from V8 SP3 or earlier versions to V9, delete the previous SSO configurations and reconfigure the SSO as described in the SSO Configuration section.
- For Visualizer V8 SP3 and earlier versions, SSO will not work for the first time due to parity issues. It will work in the subsequent executions effectively.
